Sniffed Off the Wire - Forensics (100 points)
-
● Sifting through the noise
● After weeks of perching, our avian operatives captured a suspicious network flow. Maybe there's valuable data inside?
● Solves: 58
● Download: https://cdn.squarectf.com/challenges/sniffed-off-the-wire.pcap
I like pcap challenges, so I think this was the first one I tried during this CTF after the requisite and quick classical crypto challenges. We’re given a .pcap that (refreshingly) only contains a very simple one-way stream of packets (and their ACKs):
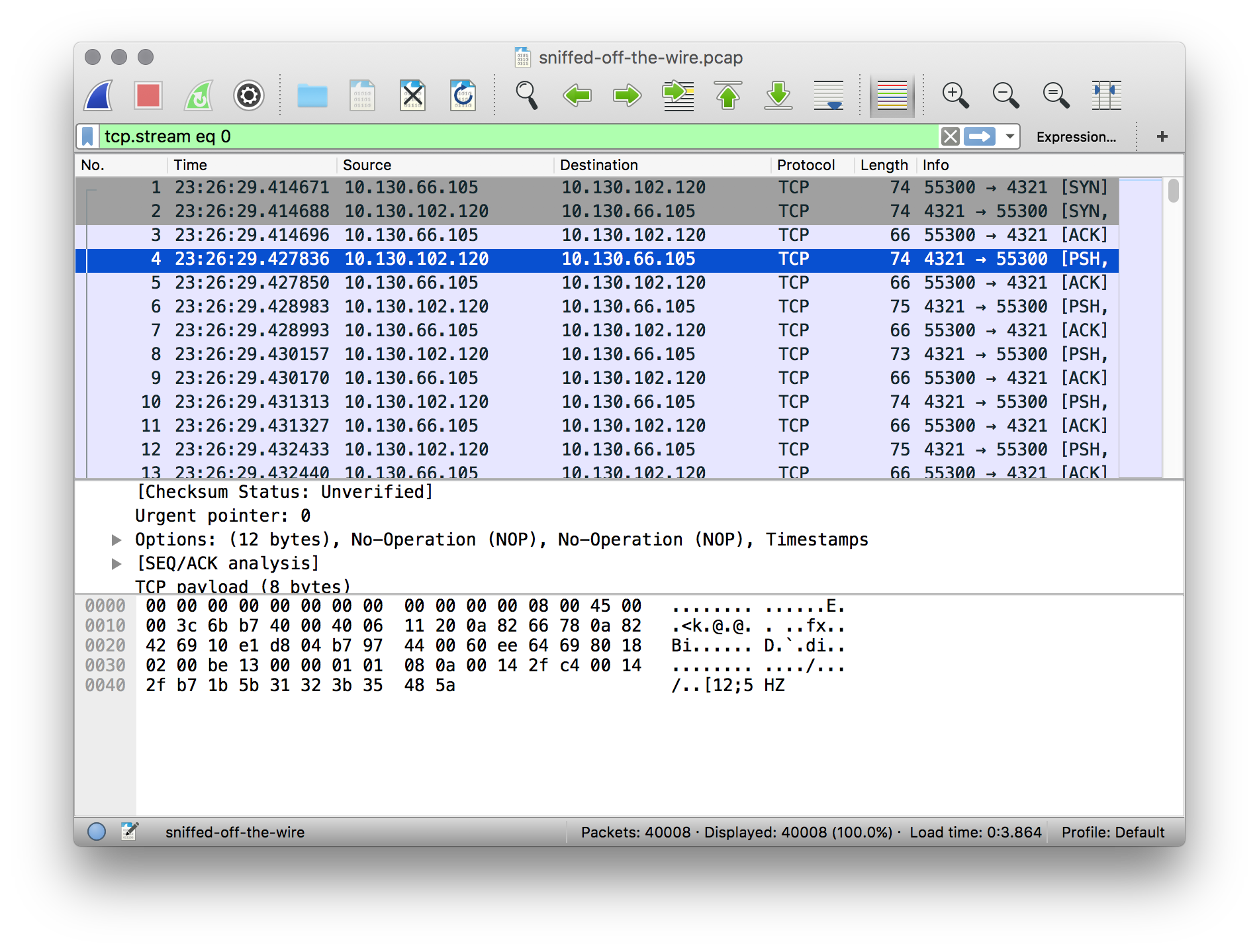
The ports don’t really mean anything to me, so let’s look at the payloads. Each payload is 7-9 bytes. We can decode the hex manually, but it’s much easier to use Wireshark’s “follow TCP stream” tool:
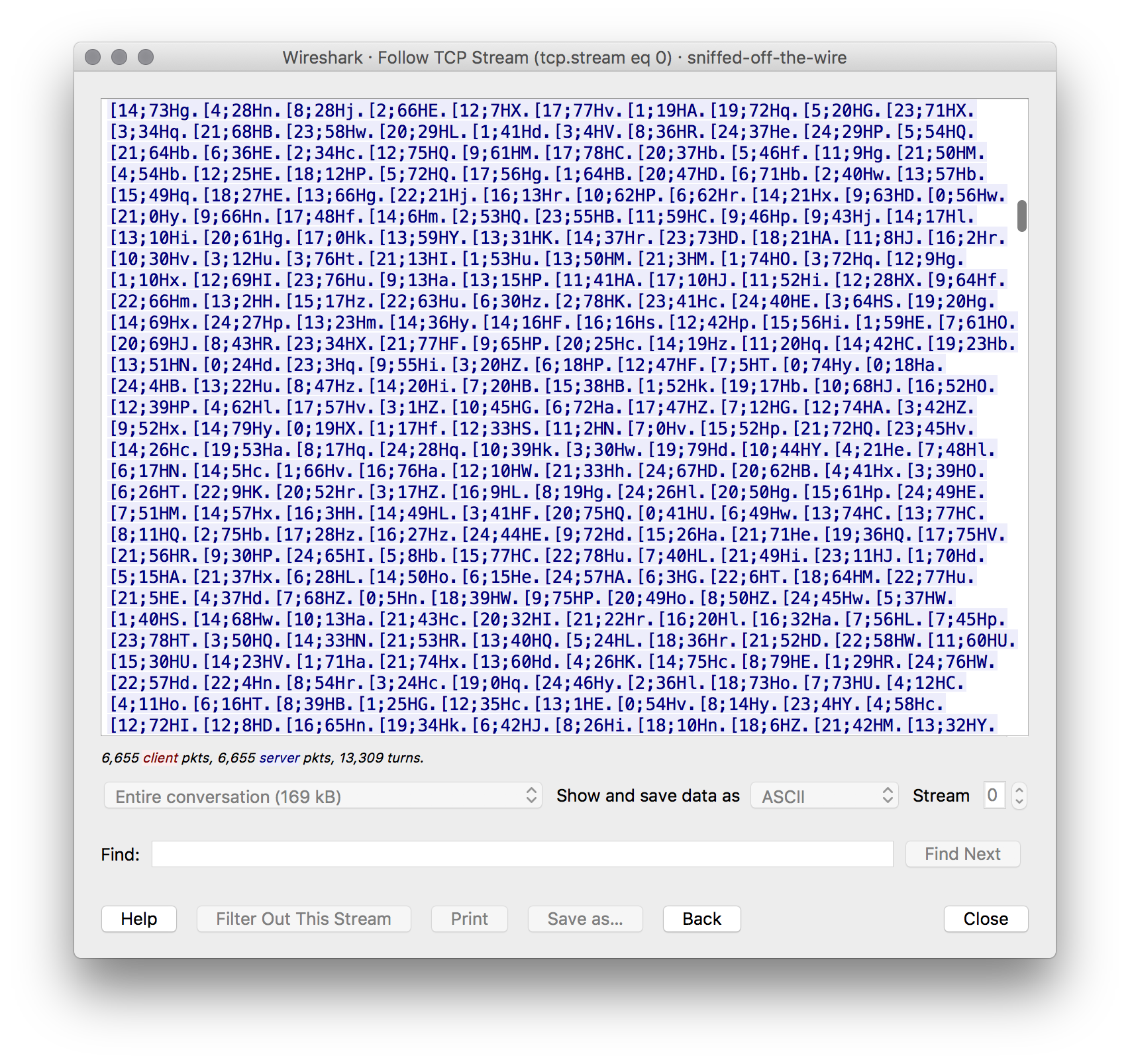
OK, that’s useful. I happen to recognize these as looking like terminal escape codes, followed by individual characters. I thought that maybe if we only look at the individual characters we’ll get something useful, but it’s not valid base64. My next try happened to work – a one-liner to cut out the payloads and pass them to xxd to unhexlify:
tshark -T fields -e data -r sniffed-off-the-wire.pcap | xxd -r -p
Here’s how it looks:
I actually ended up using asciinema just so that I could pause to copy the flag: flag-IGxKMshp46TgD3
Very cool challenge!