● 200 Points ● forensics ● By: Eric Hennenfent There are some challenges I'd rather forget. zmap.pdf
So to start, it’s a pdf, which could have any amount of craziness hidden inside it. A year or two ago, I watched a talk from an unknown infosec conference about how insane pdf is as a file format. I can’t find the talk, but it stuck with me. Anyway, we’re given what appears to be the USENIX paper on zmap. Downloading the original paper to compare, we can see that the original is 712246 bytes smaller than what we’ve been given – definitely something going on in there.
foremost is satisfied that it’s just a pdf, at least at first glance. Running binwalk -e to attempt extracting all visible files gives us 32 files of varying contents, and 32 zlib streams. Discarding the zlib streams, here’s what we have to work with:
[tkerr@pro _zmap.pdf.extracted]$ file * 10F72: ASCII text, with very long lines 11B8F7: data 11CD6B: data 14210: ASCII text, with very long lines 1D19D: ASCII text, with very long lines 1E790: ASCII text 21038: ASCII text 2114A: ASCII text, with very long lines 2244A: ASCII text, with very long lines 252CD: ASCII text, with very long lines 2B6F4: ASCII text, with very long lines 30029: data 3746: ASCII text, with very long lines 409C8: ASCII text, with very long lines 41E42: ISO-8859 text, with very long lines, with no line terminators 42598: ASCII text, with very long lines 43D53: ASCII text, with very long lines, with no line terminators 454E5: ASCII text, with very long lines 46AB0: ASCII text, with very long lines 48227: ASCII text, with very long lines 49714: PostScript Type 1 font text (CMMI10 003.002) 4B316: PostScript Type 1 font text (CMR10 003.002) 4CFCF: PostScript Type 1 font text (CMSY10 003.002) 4EF8D: PostScript Type 1 font text (MSBM10 003.002) 4F825: PostScript Type 1 font program data 5062: ASCII text, with very long lines 53EDE: PostScript Type 1 font text (StandardSymL 001.005) 549FA: PostScript Type 1 font text (NimbusRomNo9L-Medi 1.05) 5873D: PostScript Type 1 font text (NimbusRomNo9L-Regu 1.05) 5D74E: PostScript Type 1 font text (NimbusRomNo9L-ReguItal 1.05) 6212B: ASCII text, with very long lines EC5: ASCII text, with very long lines
Some of these are straightforward (fonts), and most of the ASCII files are innocent-looking pdf payloads. I happened to start from the bottom of the list, and noticed that 6212B comprises one large block of base64. Decoding it gives us a .png:

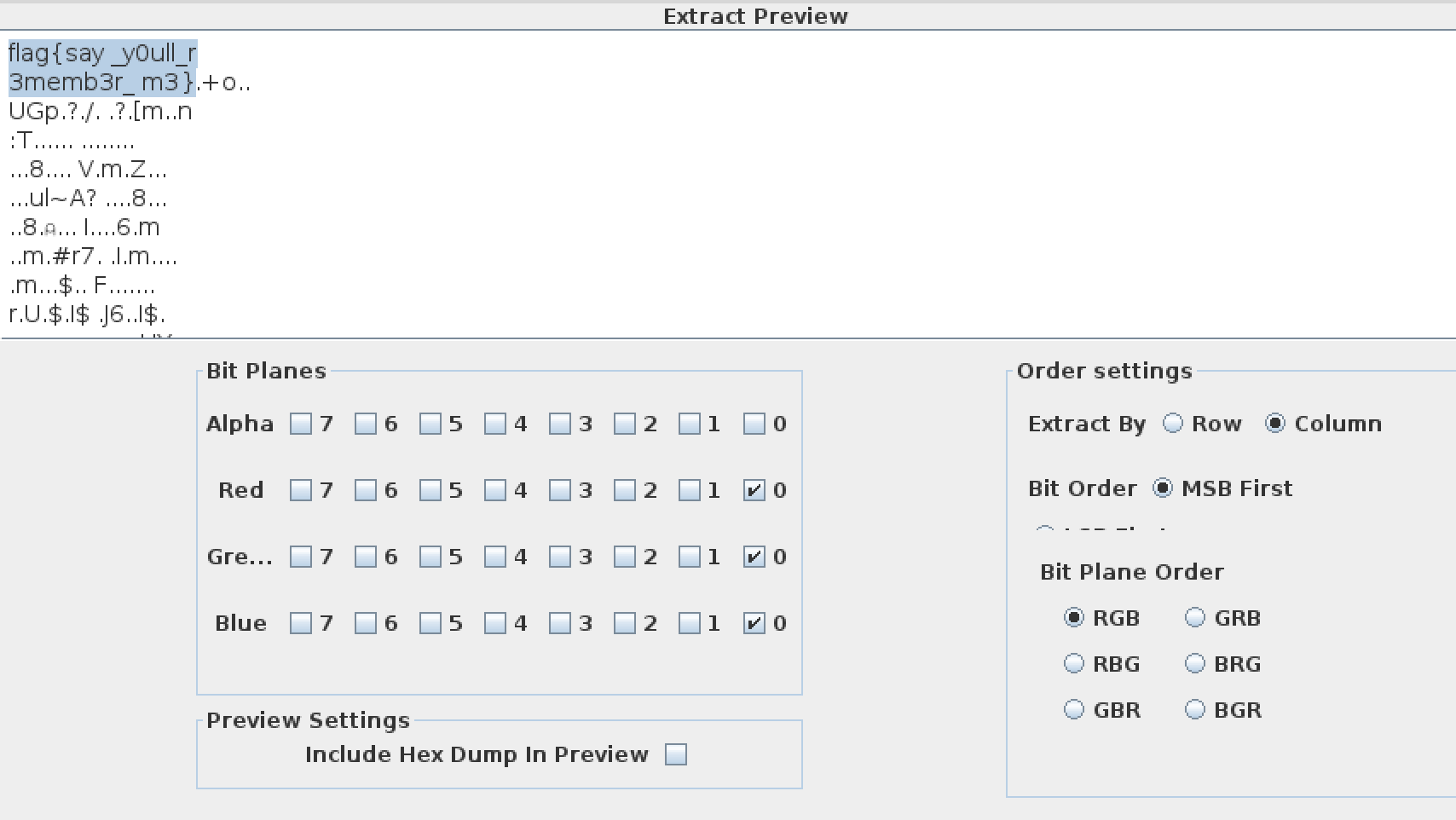
The easy first steps of strings, foremost, binwalk, and stegsolve don’t immediately give me anything promising. I reverse image search it and find an imgur album by @SwiftOnSecurity that contains the original. The dimensions of both images are the same (1221×651), but the filesizes are different, so clearly something’s been done to the file. Using imagemagick’s compare, we can see that the entire image is identical except for the very first column, at the top left:

Very suspicious. My first glance in stegsolve only involved checking the LSB data of each color channel, row-wise. Setting stegsolve to extract LSBs from all channels column-wise gives us the flag: